Luca Todesco has successfully achieved code execution in the Secure Enclave chip. Here’s everything you need to about it.
Table of Contents
Luca Todesco achieves Code Execution in SEPROM
Luca Todesco achieved code execution in SEPROM using the “blackbird” exploit a few hours ago.
A security researcher who goes by the name “Lailo” discovered a bug in the Secure Enclave chip a while ago. Based on this vulnerability, the hacker wrote an exploit called “blackbird”.
Team Pangu researchers were the first to demonstrate this SEP vulnerability at a security conference. Since the vulnerability was made public, Lailo decided to release it. Surprisingly, Team Pangu also named their exploit “blackbird”.
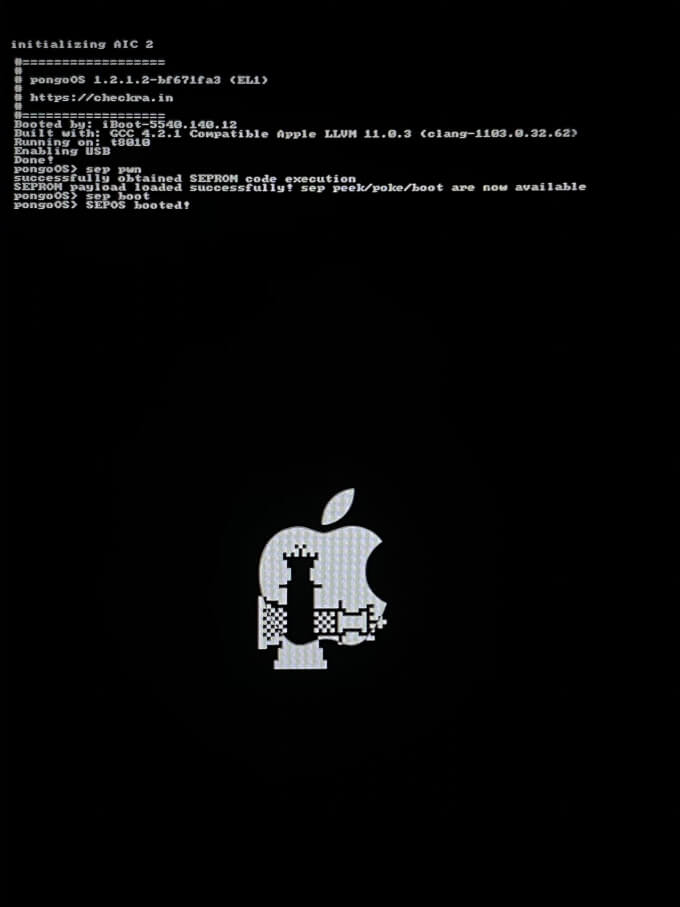
Here’s the picture Luca posted on his Twitter handle today.
The vulnerability was exploited using pongoOS – a checkra1n-based execution environment. The screen displayed the following message:
sep pwn
successfully obtained SEPROM code execution
SEPROM payload loaded successfully sep/peek/poke/boot are now available
SEPOS booted!
The hacker also posted a picture of a MacBook running the SEP vulnerability.
Todesco also remarks that every root of trust in the current lineup of Macs with the T2 security chips is compromised.
The checkra1n team intends to utilize this SEP vulnerability in the upcoming checkra1n update.
Apple has added an extra layer of protection in the Secure Enclave chip in iOS 14. This security mechanism prevents the SEP from booting in DFU mode – an essential requirement for checkra1n jailbreak.
From a jailbreak standpoint, we can bypass this protection simply by disabling the passcode. This is important for users who own a device that is incompatible with the aforementioned SEP exploit.
However, this approach also has one limitation – your device will kernel panic if you try to re-enable the passcode. The reason being that the Secure Enclave chip is able to detect if a device boots in jailbreak mode.
If a workaround is not found, you will essentially have to choose between “no passcode” and “no jailbreak”.
Security Implications of Code Execution in SEPROM
Code execution privilege in the SEPROM is a major achievement because of the following reasons:
- Firstly, it opens the doors to advanced security research in the Secure Enclave chip.
- Secondly, it allows you to jailbreak iOS 14 while keeping the passcode and Touch ID functionality intact.
The ability to hack the SEP has a lot of upsides, but it also has a few drawbacks, too. For instance, it introduces the risk of bricking devices, if not handled with care.
Moreover, it also leaves your device susceptible to intrusions by criminals and nation-state actors if they get ahold of it.
Nevertheless, we hope that the checkra1n development team will add failsafe measures to the iOS 14 jailbreak.