iTunes transfer was considered secure, but not anymore. Here’s a new vulnerability in iTunes that can allow a hacker to hijack your iPhone remotely.
Table of Contents
What is Trustjacking?
Trustjacking vulnerability exploits the iTunes Wi-Fi sync feature and grants an attacker remote access to any iPhone. This vulnerability was discovered by Symantec security researcher Roy Iarchy.
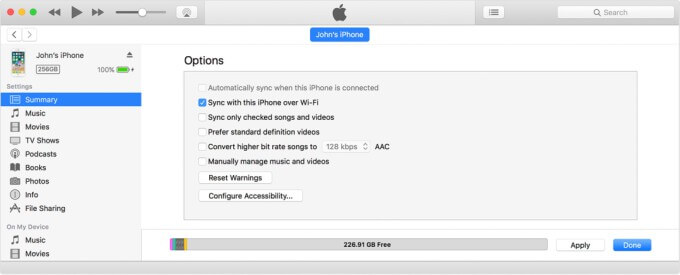
While Wi-Fi synchronization is a very useful feature, it can leave your device open to attacks.
As its name suggests, a Trustjack attack abuses the “trust” between your Apple device and a computer or charger.
Once the trust is established, a hacker can easily hijack your Apple device.
Here’s how Trustjacking works.
- The user connects his iPhone to a malicious charger or a computer via USB.
- iOS displays the “trust this computer” prompt to the user.
- The attacker forces the device to connect to iTunes and enables “iTunes Wi-Fi sync” option.
- Once these two actions are completed, the attacker will no longer require wired access to your device.
- The attacker can now control your device remotely as long as the device is on the same Wi-Fi network.
Can this attack work without Wi-Fi?
Since Trustjacking requires the attacker and the target to share the same network, the “link” between them can be broken rather quickly.
Roy and his team were able to successfully circumvent this limitation imposed by a Wi-Fi network.
They combined Trustjacking with a malicious developer profile and connected the target device to a private VPN server.
This allowed them to maintain a continuous link between the target device and the attacker’s computer thereby negating the need for a common Wi-Fi network.
How can a Trustjack attack harm your device?
Roy was able to take screenshots and access the target device’s screen in real-time.
Hackers can also access and even create a new iTunes backup, containing all your private data, from scratch.
This will essentially reveal all private data like photos, iMessage chats, WhatsApp chat history, etc. stored on the target device.
But wait, there’s more! The attacker can also replace existing applications with malicious repackaged versions or even install new apps on your device. This could easily be utilized to spy on your activities.
All in all, the attacker can perform all actions that a user can perform via iTunes.
For more iOS security updates, follow us on Twitter and Facebook.