German developer Opa334 has made a startling revelation on Twitter. He revealed that MainRepo.org injects malware onto jailbroken devices. Here’s all you need to know about it.
Table of Contents
MainRepo.org installs malicious files on jailbroken devices
MainRepo, a well-known repository in pirate circles, has been sneakily injecting malware onto jailbroken devices.
Renowned tweak developer Opa334 recently blew the lid off the scam with a flurry of tweets targeting the repo.
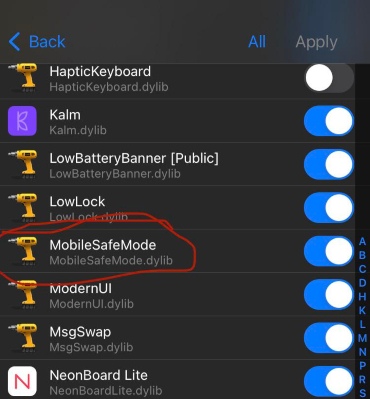
The mainrepo malware ("MobileSafeMode.dylib") sends your UUID to a server, the server then has the ability to send back any command that should be executed on your device. It's essentially a backdoor that's running inside SpringBoard and Cydia. pic.twitter.com/QcY4rFnRDg
— opa334 (@opa334dev) March 23, 2021
The malicious dylib file “MobileSafeMode.dylib” allows the attacker to execute shell commands on compromised Apple devices. It also fetches the device’s serial number, Mac address, and ECID.
Essentially, it is a backdoor running inside the SpringBoard.
MobileSafeMode.dylib malware (via @opa334dev)
Here’s the complete list of malicious files that MainRepo installs on your device:
- MobileSafeMode.dylib
- RocketBootstrapUI.dylib
- SnowBoardSB.dylib
- MainRepoEGG.dylib
The malware has been carefully crafted with names that resemble those of general tweak files, so as not to arouse suspicion. All of the files have the same content and the same SHA256 hash.
ESET research also confirmed Opa334’s findings on its Twitter handle.
#ESETresearch can confirm this great find by @opa334dev. The mentioned dylib binary is indeed malicious iOS tweak that allows the attacker to execute shell commands on a jailbroken and compromised iOS device @cherepanov74 1/5 https://t.co/bdGCX2mTBx
— ESET research (@ESETresearch) March 25, 2021
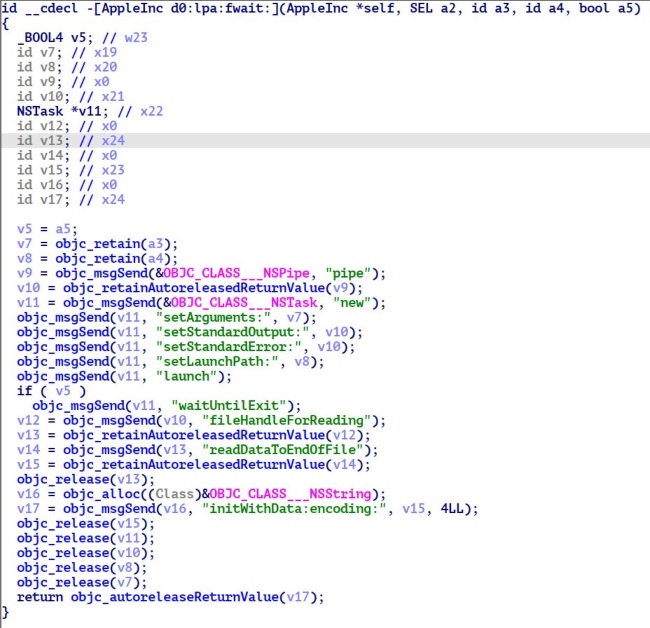
Per ESET research, the malware downloads a JSON file, which contains a list of commands to run on an affected device, from its command-and-control center.
The botnet administrator can then run specific commands on your Apple device using its UDID (Unique Device Identifier).
MainRepo administrators utilize crux – a tool that allows you to run commands with root privileges on a jailbroken iPhone. The user’s sensitive data is then exported through the Telegram Bot API.
The malware uses the http://app-le.me/ domain, which has since been taken down, to transmit user information.
MainRepo admin hit back at Opa334
Opa334 decided to join the MainRepo Telegram group and posted a string of messages about how the malware works.
As expected, the developer was banned instantly from the group and all messages were removed.
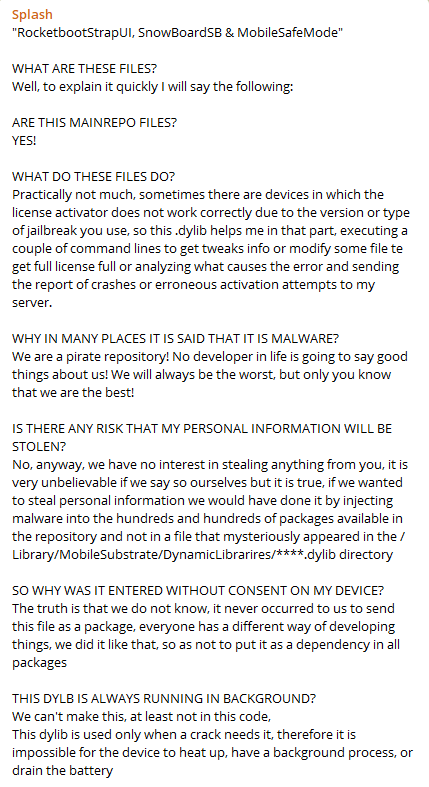
Splash, the admin of the Telegram group, decided to clear the air with a long-winded response. However, his weak rebuttal does not inspire much confidence in their shady practices.
These malicious dylib files are not used to crack Cydia tweaks at all. For example, “DiskProbeHack.dylib” is used to crack DiskProbe, not “MobileSafeMode.dylib”.
How to keep your device safe from MobileSafeMode.dylib malware
MainRepo users should immediately remove the malicious files and hope they did not send sensitive data to their servers.
We also recommend removing pirated tweaks changing passwords just to be on the safe side.
If you have iCleaner installed on your iPhone or iPad, tap the file name and check its dependencies, that is, the tweaks that require this file to be installed.
The MainRepo fiasco underscores the importance of keeping your jailbroken device secure at all times.
Don’t ever pirate jailbreak tweaks and always use official repositories for installing tweaks.
Remember, there’s no such thing as a free tweak. You can’t expect anyone to hand out paid stuff for free in this day and age.
If you don’t pay with your money, you pay with your privacy. If someone is indeed giving stuff away for free, chances are your data is being collected.