Patrick Wardle exploited Apple’s computer operating system using “invisible” clicks at Defcon 2018. Here’s how the “synthetic event” vulnerability works.
Table of Contents
The mouse is mightier than the sword
Kernel Extensions (KEXT) are modules of code that run directly inside the kernel and are not subject to the same security policies as normal programs.
Developers often implement device drivers as kernel extensions. But because the kernel and its extensions do not have the same security policies as normal programs, they are a popular target for hackers.
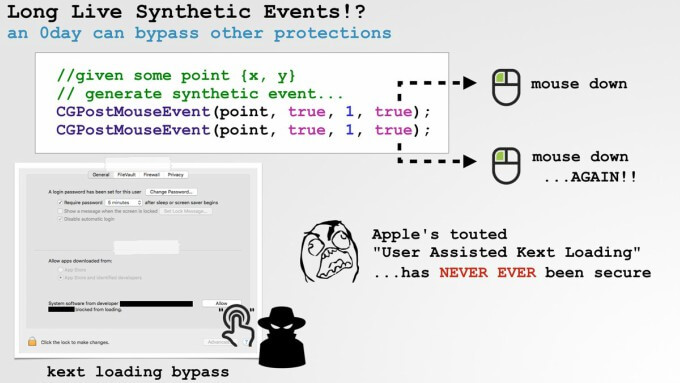
In macOS 10.13 High Sierra, users must authorize the installation of kernel extensions from system settings before the system loads and executes them.
However, security researcher Patrick Wardle found that installing kernel extensions is possible using synthetic events.
In macOS 10.13 High Sierra and older versions, the mouse position can be set from an app and clicks can be simulated. This makes it possible for an app to install kernel extensions without user’s permission.
Diving deeper into the macOS rabbit hole
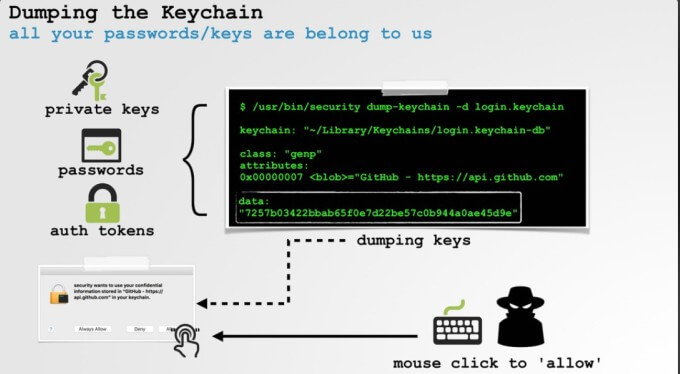
Diving deeper into macOS, Wardle discovered that synthetic clicks can also be used on requests involving sensitive user data like contacts, calendar, or location.
What’s more, these events can also uncover private keys, passwords could also be used to access all stored keys.
This could allow a cybercriminal to have access to important aspects of the system.
Since users can easily detect invisible clicks, Patrick proposes a few interesting techniques to make these attacks “invisible”, namely –
- Set the display brightness to zero.
- Detect inactivity before dimming the brightness level.
Wardle also uploaded slides of his Defcon talk on his Patreon page. You can check out the “The Mouse is Mightier than the Sword” slide here.
What are synthetic clicks?
Synthetic clicks, also known as “invisible” clicks, allow some programs to generate clicks that are not performed by the user. A relevant example is Apple’s very own AppleScript scripting language.
These clicks are actually intended for automation and execution of functions for people with disabilities. However, in some cases, synthetic clicks are disabled for security reasons.
Apple has patched this vulnerability in macOS 10.14 Mojave. Although synthetic clicks are still a part of macOS, the user must first grant them the necessary permissions.