Security researcher Qixun Zhao of Qihoo 360 Security Team has released Chaos vulnerability for iOS 12.1.1. The hacker also demonstrated a remote Safari jailbreak for iOS 12.1.1 and below versions on an iPhone XS.
Table of Contents
Qixun Zhao makes Chaos proof-of-concept public
In November 2018, Qixun Zhao aka S0rryMybad demonstrated a remote jailbreak on A12 devices at the TianfuCup PWN Contest.
Termed “Chaos”, this kernel vulnerability discovered by Zhao can be triggered directly in the sandbox.
Since this vulnerability allows RCE (Remote Code Execution), we can trigger it from the mobile Safari web browser, thus jailbreaking the device remotely.
IPC Voucher UaF Remote Jailbreak Stage 2 https://t.co/V8prQKAllh (Chinese, English may be later) and demo : https://t.co/lf6aY4nRDc
— SorryMybad (@S0rryMybad) January 23, 2019
S0rryMybad also posted a video of the remote jailbreak he developed on the Chinese website Youku. We have reposted the video from his Youku account on Twitter.
The video showcases a remote jailbreak running on two iPhone XS devices. The hacker then opens the jailbreak website (192.168.1.52) that injects the exploit and then resprings the device in the jailbreak mode.
iOS 12.1.1 remote jailbreak demonstrated on iPhone XS, PoC of Chaos kernel vulnerability to be released soon (dev – @S0rryMybad). #RETWEET for visibility pic.twitter.com/xDPLQpfuLX
— Yalu Jailbreak (@Yalujb) January 23, 2019
After successfully jailbreaking the iPhones, S0rryMybad proceeds to launch Mobile Terminal, which confirms that the hacker has gained root access on iOS 12.1.1 firmware.
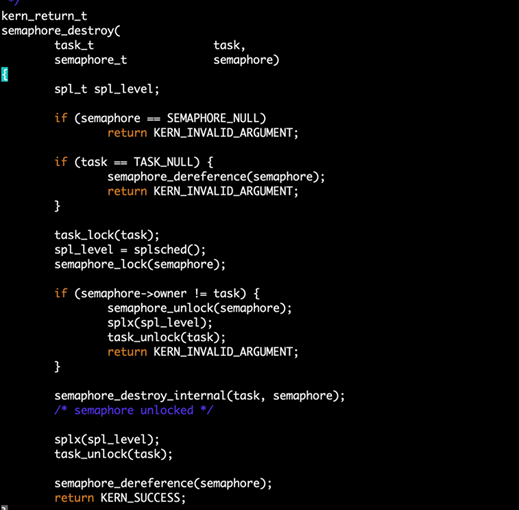
How the Chaos kernel vulnerability works
The iOS kernel contains a component called MIG, generated automatically by the .defs file.
Generally, MIG performs inter-core object conversion and object reference count management, and then calls kernel methods.
If the firmware developer is not familiar with MIG management, improper management of the reference counts of kernel objects can leak the reference counts, allowing hackers to circumvent the defenses.
Although the proof-of-concept for Chaos vulnerability is now public, Qixun has made it very clear that he doesn’t intend to make the exploit source code public.
If developers are keen on developing an iOS 12 jailbreak, they will have to put the pieces of the puzzle together and complete the exploit on their own.
This also includes the post-exploitation code that developers use in the later stages of jailbreak development.
What next for the jailbreak community?
According to Tihmstar, we can use the Chaos proof-of-concept to develop an exploit for iOS 12.1.1 and below versions.
This can be achieved by copy-pasting the PoC in v0rtex exploit for iOS 10.3.3, replacing some of the code from jelbrektime, and then adding the correct offsets.
Since Apple is still signing iOS 12.1.1 firmware, I highly recommend jumping on it before the signing window shuts – if and only if you are on a higher version.
Now that iOS 12.1.3 final update is out, fire up iTunes and download the iOS 12.1.1 (final) IPSW firmware file.



Nice and very technical article
though some will never understand.
Still on sweet olde’ ios 12.0.1 so I think I’m good
Thanks for the kind words, David.